
Information Security
Basic Policy
The Elan Group (hereinafter referred to as “the Group”) is enhancing its information security foundation as a part of its corporate social responsibility, creating an enriching living environment. We will continue to identify information security risks, including cyberattacks, treat information security as a key management priority, and strive for continuous improvement.
Governance of Information Security
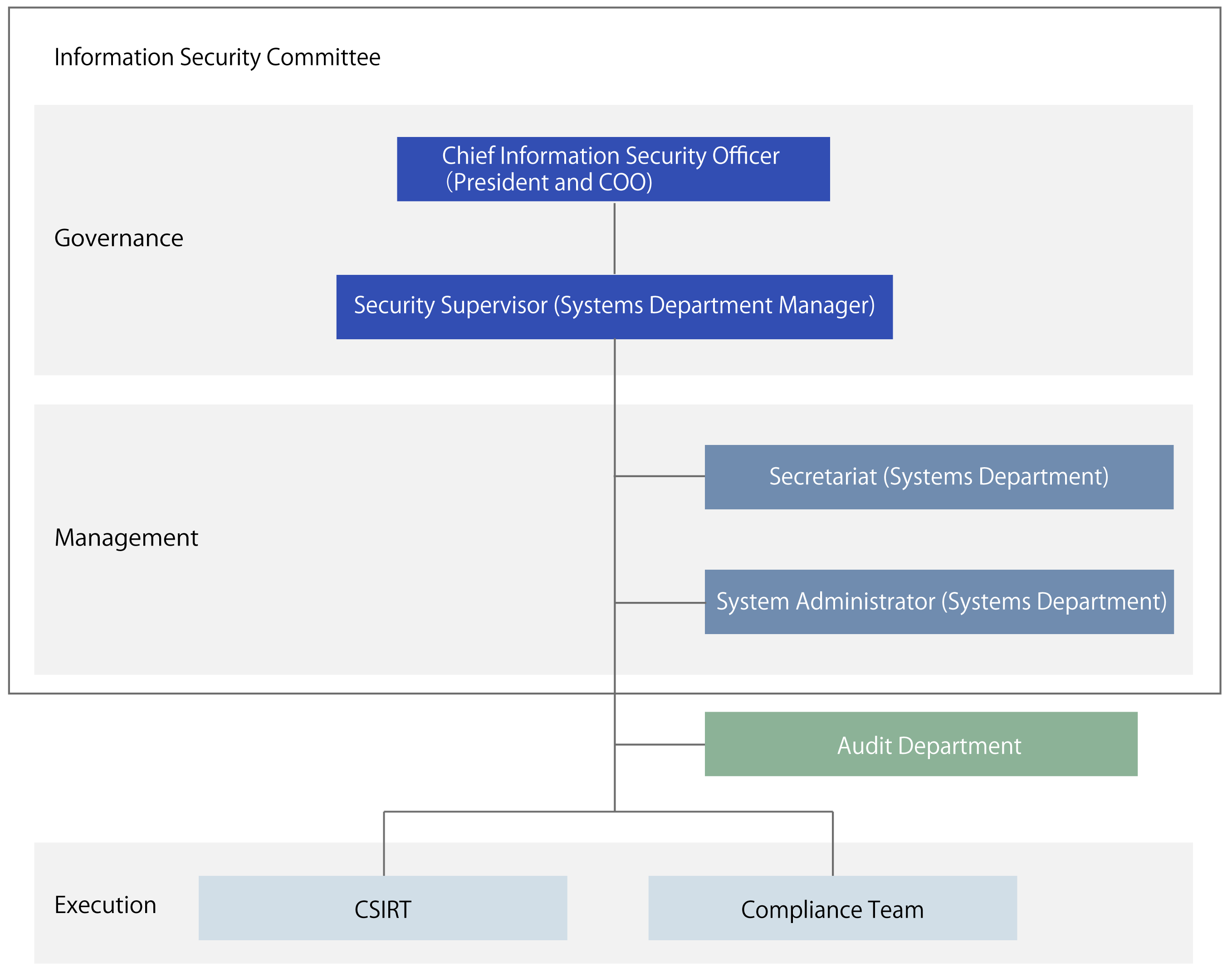
Elan has established an information security governance system that aligns with our overall corporate governance structure. The system comprises an executive function led by the Chief Executive Officer (CEO) and a supervisory function carried out by the Board of Directors (BoD) to oversee the executive function. In terms of the former function, the CEO is accountable to the BoD and external stakeholders regarding information security. The Information Security Committee and its dedicated team under the jurisdiction of the CEO are responsible for implementing these measures, and they supervise the formulation and implementation of group-wide risk management and strategies related to information security. In terms of the latter function, the CEO holds the ultimate responsibility for oversight as part of our overall corporate governance framework. The CEO regularly reports to the BoD on the status of information security across the entire Group, and also reports any changes in the environment as needed. Additionally, more frequent and regular reports are made to the Audit & Supervisory Committee.
For a more detailed implementation structure, we define the necessary security functions for each of the three layers: the governance layer, which oversees the formulation and implementation of information security strategies for the entire Group; the management layer, which plans and oversees execution within each function and department based on the formulated strategies; and the execution layer, which handles the actual execution within each function and department. This approach ensures an effective, efficient, company-wide strengthening of the system.
We are also working to build security systems optimized for each domain, including information security for general IT systems and data governance (enterprise security), and information security for our services (product security). Furthermore, we are enhancing the system under the direction of the General Manager in Charge of Personal Information Protection Management to ensure thorough understanding and compliance with important laws and internal regulations related to personal information protection (privacy compliance). (https://www.kkelan.com/privacy/)
Regarding risk management, the Security Supervisor and his/her team conduct risk assessments for the entire Group, considering various external factors such as trends in cyberattacks outside the Company and industry best practices. Based on these risk assessments, they formulate medium-term strategies that align with our business strategy, customer needs, and regulatory trends. Then, by implementing risk reduction measures based on the strategies formulated by each function and department, we ensure balanced risk reduction across the Group according to unified standards.
For our crisis management system, three aspects are important in the event of a cyberattack: swift response, coordination with the entire Group and related organizations, and decision-making by management. Therefore, we are working to establish a Computer Security Incident Response Team (CSIRT) to ensure rapid incident containment and recovery.
Cybersecurity Strategy
To counter cybersecurity threats, we will deploy various security technologies at each layer—perimeter, internal, and endpoint—to address increasingly sophisticated attacks, thereby protecting our information assets through a multilayered defense.
As part of this effort, we have started monitoring cyberattacks and responding quickly to alerts regarding malware, including ransomware. We also conduct incident response drills based on real incidents and review our response procedures.
We continue to make ongoing improvements and enhancements to our computers to adapt to evolving threats, such as installing anti-malware software that detects malicious behavior to stop all types of attacks before they compromise our systems.
Personal Information Management
Elan maintains a personal information protection management system that complies with JIS standards (JIS Q 15001) and the Act on the Protection of Personal Information. Under the personal information protection policy outlined below, we take measures to ensure that all directors, officers and employees are informed of this policy and that it is easily accessible to the general public. We will strive to protect personal information appropriately in accordance with this policy. (Personal Information Protection Policy) Note: Elan has been awarded the PrivacyMark by the Japan Institute for Promotion of Digital Economy and Community (JIPDEC), certifying our proper handling of personal information.
Education Initiatives
We conduct annual information security training for all employees, in addition to training for each employee level, such as for new recruits and newly appointed managers. We also regularly provide education and training on our Privacy Policy and proper handling of personal information to enhance security awareness and skills. Additionally, we are publishing a series of articles on information security in our company newsletter to enhance literacy among all employees.








